As churches rely more on technology, strong church cybersecurity is essential to protect communication, donations, and events. While new tools and technology create opportunities, they also introduce risks. Many faith-based organizations assume they are unlikely targets for cybercriminals. However, weak security practices make churches attractive to attackers looking for financial data, donor information, and system access.
In fact, A 2025 article by Dami Olusanya highlights that ministries and nonprofits account for nearly 43% of all cyberattacks in North America alone. Without a structured plan, churches remain vulnerable to attacks that could disrupt operations and damage trust within the congregation.
Understanding the threats, identifying weak spots, and establishing security policies can help protect your church’s digital infrastructure. Partnering with a Tech Advisor like Lamb Telcom can provide the guidance needed to build a church cybersecurity strategy that scales with your organization.

Understanding the Threat Landscape
Why Churches Are Targeted
Cybercriminals often focus on organizations that lack formal security policies. Churches fall into this category because they tend to prioritize accessibility over restrictions. Volunteers and staff members handle sensitive information, yet many operate without cybersecurity training. This combination makes faith-based organizations an easy target.
Common reasons churches face cyber threats include:
- Valuable Data – Churches store a significant amount of personal information, including names, addresses, phone numbers, and financial records of members and donors. Many also use online donation platforms that process credit card and banking details, making them a prime target for attackers looking to steal sensitive financial data.
- Trust-Based Culture – Churches foster an open and welcoming environment, which cybercriminals exploit through impersonation tactics. Scammers send emails pretending to be pastors or church staff, requesting money transfers or login credentials, knowing that people are more likely to trust a familiar name.
- Limited IT Resources – Many churches operate without dedicated IT personnel, which means system updates, security patches, and network monitoring are often inconsistent or nonexistent. Without ongoing oversight, vulnerabilities go unnoticed, giving cybercriminals an opportunity to break in.
- Outdated Systems – Some churches continue using old hardware and unsupported software because replacing them can be costly. Unpatched operating systems, unsecured Wi-Fi networks, and weak passwords leave church internet connections exposed to cyber threats.
Common Cyber Threats for Churches
Understanding the risks can help your church take proactive steps to prevent attacks. The most frequent cyber threats include:
- Phishing Attacks – Attackers send emails that look like they’re from a trusted source, such as a church leader or a well-known vendor. These messages often include urgent requests for payments, password resets, or confidential information. Once a staff member clicks a fraudulent link or downloads a malicious file, hackers gain access to sensitive church data.
- Ransomware – Cybercriminals encrypt church files and demand payment before restoring access. This type of attack can lock up financial records, sermon archives, and member directories, leaving the church unable to function until a ransom is paid. Some organizations never recover their data, even after paying.
- Unauthorized Access – Weak passwords and shared login credentials make it easy for hackers to gain control of church email accounts, donation systems, and internal networks. Once inside, they can redirect financial transactions, send fraudulent messages, or steal private information.
- Data Breaches – Hackers break into church internet systems to steal donor information, membership records, and login details. This data can be sold on the dark web or used for identity theft, putting members at risk and damaging trust within the congregation.
Recognizing these risks is the first step toward strengthening security. The next step is identifying where your church may be vulnerable, assessing the impact of a potential attack, and taking preventive measures to protect church internet systems and sensitive data.
Assessing Organizational Risk
Identifying Vulnerabilities
Church cybersecurity challenges are unique. Conducting an assessment can help pinpoint areas that need improvement.
Consider the following questions:
- Do staff and volunteers use personal devices for church communication?
- Are login credentials shared between multiple people?
- How often are software updates and security patches applied?
- Is the church internet network secured with strong encryption?
- Are financial transactions monitored for suspicious activity?
These gaps create opportunities for cybercriminals to access systems and data. A risk assessment helps uncover weak spots before they become serious issues.
Steps to Evaluate Security Risks
- Review Access Controls – Determine who has permission to view and modify sensitive church records. Restrict access to financial and member data.
- Test Password Strength – Ensure staff and volunteers use complex passwords and enable multi-factor authentication (MFA) where possible.
- Check Device Security – Verify that church-owned computers, tablets, and phones have updated security software. Encourage personal device protections for staff working remotely.
- Train Staff and Volunteers – Provide cybersecurity awareness training so they can recognize threats and follow security guidelines.
- Monitor Network Activity – Review church internet usage to detect unauthorized access or unusual activity.
A thorough assessment sets the foundation for effective security policies. Once risks are identified, churches can develop structured guidelines to reduce exposure.

Developing Core Church Cybersecurity Policies
Policies create consistency in how your church handles security. They provide clear expectations for staff, volunteers, and leadership. Here are the key policies every church should consider.
Access Control and Password Management
- Assign unique logins for staff and volunteers instead of sharing accounts.
- Require strong passwords that include a mix of uppercase, lowercase, numbers, and symbols.
- Enable multi-factor authentication (MFA) for email, financial accounts, and other critical systems.
- Remove access for former employees and volunteers immediately after their departure.
Secure Communication and Email Policies
- Use official church email addresses instead of personal accounts for church business.
- Implement spam filters to reduce phishing emails.
- Train staff to verify suspicious emails before clicking links or opening attachments.
- Encrypt sensitive messages, especially those involving financial or personal data.
Safe Donation and Financial Practices
- Use reputable donation platforms with security measures in place.
- Set up alerts for unusual transactions.
- Require dual authorization for financial transfers to prevent fraud.
- Regularly review financial statements to catch unauthorized activity.
Incident Response Planning
- Establish a plan for responding to cybersecurity incidents, including ransomware attacks and data breaches.
- Designate specific individuals to handle security events.
- Have backup systems in place to restore lost data without paying a ransom.
- Communicate clearly with the congregation if an incident affects church operations.
Policies should be reviewed and updated regularly to adapt to new threats. However, many churches struggle to enforce these measures due to limited resources. This is where common mistakes arise.

Common Church Cybersecurity Gaps & Mistakes
Churches often overlook critical areas in their cybersecurity planning, leaving them vulnerable to various threats. Addressing these common mistakes can significantly enhance your church’s cybersecurity posture:
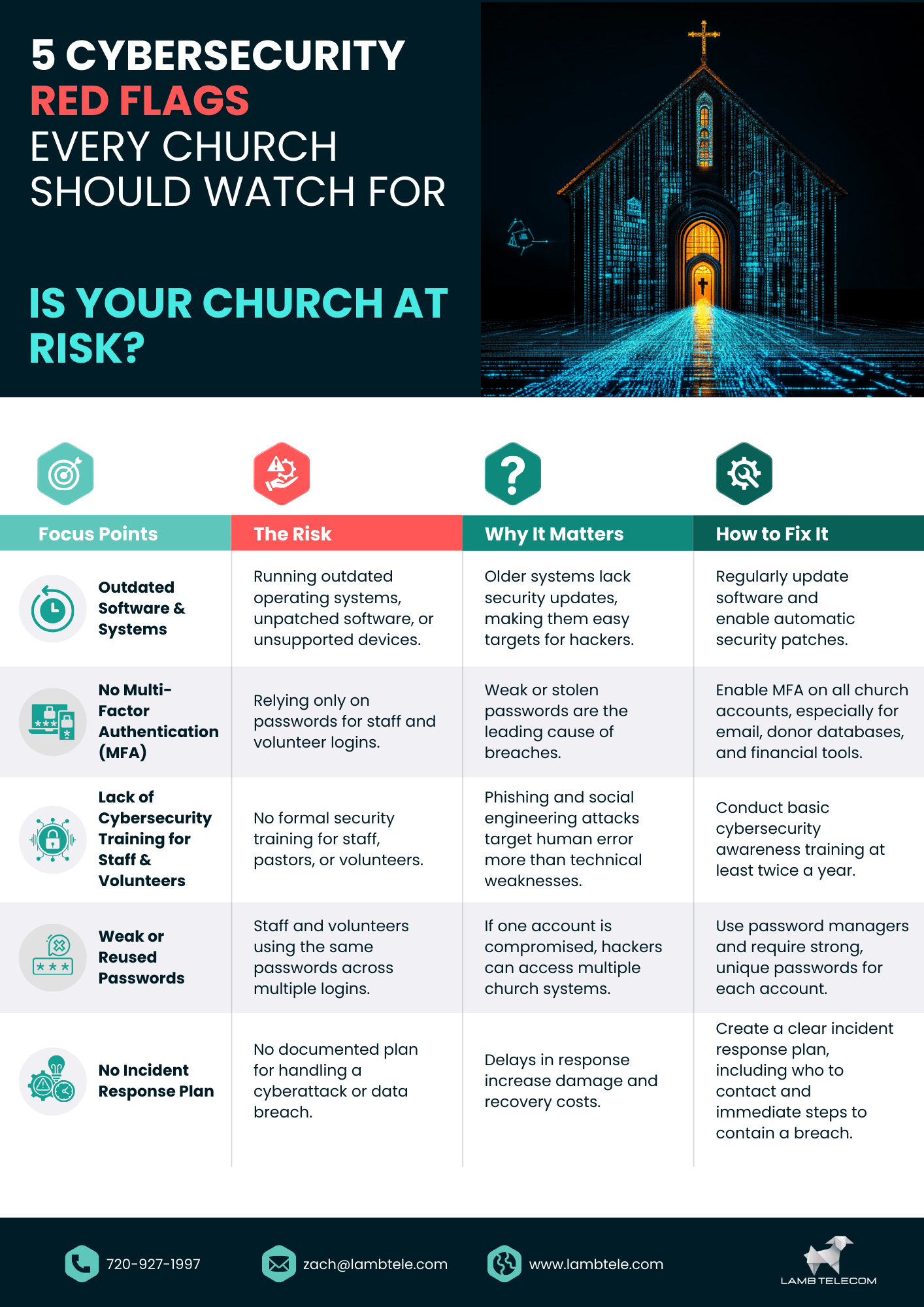
- Believing Cyber Threats Won’t Target Churches – Many assume hackers focus solely on businesses, overlooking that faith-based organizations are also targets. This misconception leads to complacency, making churches with weak security attractive to cybercriminals.
- Relying on Outdated Technology – Using old computers and software without necessary security updates exposes systems to attacks. For instance, the UK government’s National Audit Office reported that in 2024, 58 critical systems had significant cyber-resilience gaps due to outdated technology.
- Neglecting Staff and Volunteer Training – Without proper cybersecurity training, employees and volunteers may unknowingly fall for phishing scams or use weak passwords. According to Fortinet’s 2024 Security Awareness and Training Global Research Report, 67% of organizations are concerned that employees lack fundamental security awareness.
- Failing to Secure Personal Devices – Staff members often use personal laptops and phones for church work. Without proper security settings, these devices can become entry points for cybercriminals, compromising the church’s network and sensitive information.
- Skipping Regular Security Audits – Churches that don’t periodically check for vulnerabilities remain exposed to evolving threats. Regular audits help identify and address security gaps before they can be exploited by attackers.
By recognizing and addressing these common gaps, your church can strengthen its defenses, protect sensitive data, and maintain the trust of your congregation.

The Role of a Tech Advisor in Church Cybersecurity
A Tech Advisor helps churches develop and maintain strong cybersecurity strategies, ensuring that faith-based organizations can operate securely without disruptions. Unlike general tech consultants, Lamb Telecom specializes in working with churches, understanding the unique balance between accessibility, ministry operations, and security. Instead of taking a reactive approach, an advisor focuses on long-term protection, reducing risks before they turn into serious threats.
1. Conduct Security Assessments
A Tech Advisor evaluates your church’s entire digital infrastructure, identifying weak points that could expose sensitive information. This includes assessing your church internet setup, email security, data storage, and access controls to ensure that vulnerabilities are addressed before they are exploited.
2. Implement Security Measures
Once risks are identified, an advisor helps put protective measures in place to safeguard your systems. This can include setting up multi-factor authentication, securing Wi-Fi networks, restricting access to financial data, and ensuring that software updates and patches are applied regularly.
3. Provide Training and Support
Cybersecurity is not just about technology—it’s also about the people using it. A Tech Advisor educates staff and volunteers on best practices, such as recognizing phishing emails, using strong passwords, and securing their personal devices when accessing church systems.
4. Monitor Systems and Respond to Threats
Cyber threats can strike at any time, making ongoing monitoring crucial. A Tech Advisor helps track suspicious activity and responds quickly to potential breaches, preventing financial loss, data leaks, and disruptions to ministry operations.
5. Ensure Compliance with Data Protection Standards
Churches handle a large amount of personal and financial data, making compliance with security regulations a priority. A Tech Advisor helps implement policies that align with legal and ethical guidelines, ensuring that member and donor information is handled responsibly and securely.
Partnering with an advisor allows your church to focus on its mission while maintaining a secure and trustworthy environment for your congregation.

Protect Your Church Internet & Data Before It’s Too Late
Cybersecurity threats pose real risks for churches, but a proactive approach can prevent attacks. By assessing vulnerabilities, creating security policies, and addressing common mistakes, your church can build a safer digital environment.
A Tech Advisor can provide the guidance needed to develop a scalable security strategy. Don’t wait until a breach occurs—take action now to protect your church’s data, finances, and reputation.
Schedule a consultation with Lamb Telecom’s IT experts today to strengthen your church’s cybersecurity strategy.